Intrusion Detection Systems in Cybersecurity: Safeguarding the Digital Frontier In today’s digital age, cybersecurity has become a top priority for organizations and individuals alike. As we rely increasingly on technology for communication, business operations, and personal activities, the risks posed by cybercriminals have grown significantly. Intrusion Detection Systems (IDS) play …
Read More »Exploring the Applications of Holographic Technology
Exploring the Applications of Holographic Technology Holographic technology has captivated the imagination for decades, often depicted in science fiction as a futuristic tool capable of creating 3D representations of objects and people. While the concept has long been associated with sci-fi movies and visionary predictions, recent advancements in science and …
Read More »Molecular Computing: An Alternative to Silicon-Based Computers
Molecular Computing: An Alternative to Silicon-Based Computers The world of computing has undergone dramatic transformations since its inception. From mechanical calculators to the microprocessor-driven machines that power everything from smartphones to supercomputers, technological advancements continue to push the boundaries of what is possible. However, as demand for more powerful, energy-efficient, …
Read More »5G Technology: Exploring the Cybersecurity Implications
5G Technology: Exploring the Cybersecurity Implications The advent of 5G technology marks a significant leap forward in telecommunications, promising faster speeds, lower latency, and a more reliable internet connection. With the growing reliance on the internet for everything from remote work to healthcare, 5G will enable new opportunities for innovation …
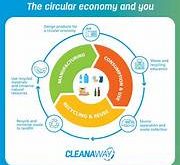
Read More »Plastic Recycling Technology: An Approach Toward Circular Economy
Plastic Recycling Technology: An Approach Toward Circular Economy In recent years, the growing awareness of environmental issues has sparked a global conversation about waste management and the sustainability of the products we use every day. Among the various materials contributing to the global waste crisis, plastic has emerged as a …
Read More »Application and Limitations of Homomorphic Encryption in Cloud Computing
Application and Limitations of Homomorphic Encryption in Cloud Computing In the age of cloud computing, security remains a major concern for users and businesses alike. The cloud provides the convenience of storing and processing vast amounts of data remotely, but it also raises significant concerns regarding the privacy and integrity …
Read More »Nano-Scale Communication: Challenges in Network Design
Nano-Scale Communication: Challenges in Network Design The concept of nano-scale communication represents one of the most fascinating frontiers of modern technology. It involves the transmission of information among devices or systems operating at the nanometer scale—ranging from molecular to atomic levels. These devices are not just a distant dream; they …
Read More »Analyzing the Security Measures in Next-Generation 6G Networks
Analyzing the Security Measures in Next-Generation 6G Networks As the world transitions from 5G to the next-generation 6G networks, the demand for faster, more reliable, and secure communication systems has never been greater. 6G promises to revolutionize various sectors, including healthcare, education, manufacturing, and entertainment, by providing ultra-low latency, high-speed …
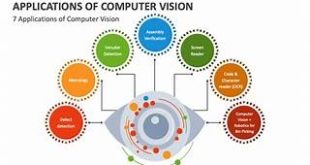
Read More »Computer Vision and Image Understanding: Advanced Techniques and Applications
Computer Vision and Image Understanding: Advanced Techniques and Applications In the modern digital age, the realm of computer vision has grown to be a key pillar of artificial intelligence (AI). The task of enabling machines to see, interpret, and make decisions based on visual inputs has vast implications across industries, …
Read More »Advanced Intrusion Detection Systems in Cybersecurity: New Approaches
Advanced Intrusion Detection Systems in Cybersecurity: New Approaches In an increasingly digital world, the demand for robust cybersecurity measures has never been greater. Advanced Intrusion Detection Systems (IDS) play a pivotal role in safeguarding networks, data, and digital infrastructure from evolving threats. This article explores new approaches to IDS, focusing …
Read More »